In this guide, we will look at the key technological elements that make up the blockchain and their overview. To understand the structure of the blockchain, there is a very easy-to-understand website (the site by Mr. Anders Brownworth), so let’s deepen our understanding using this site.
The Data Structure of Blockchain
Cryptographic Hashes
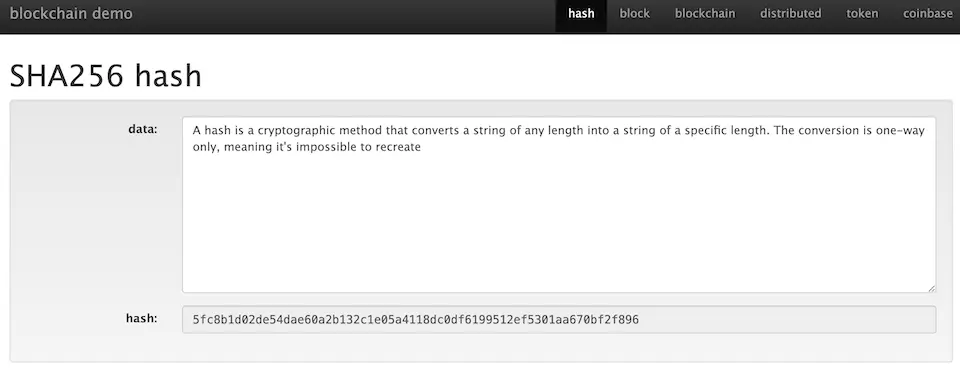
A hash is a cryptographic method that converts a string of any length into a string of a specific length. The conversion is one-way only, meaning it’s impossible to recreate the original data from the cryptographic result (irreversibility).
There are various types of hash cryptography, and in the case of Ethereum, the keccak256 method is used. The hash demonstration page on the aforementioned site uses the SHA256 method. Both are 256-bit (32-byte) data. In the image below, the ‘Data’ section represents any input string, and the cryptographic result is displayed in the ‘Hash’ section. The result is expressed in characters ranging from 0 to 9 and a to f (hexadecimal). When you modify the input string, the result value also changes
Blocks in Blockchain
In English, blockchain can be decomposed into ‘Block’ – ‘Chain’. In essence, it is a structure where multiple blocks are connected like a chain. So, what exactly is a block? A block refers to a unit of data clump. Broadly speaking, in the case of blockchain, a clump of data with a structure like in the image is referred to as a block (as shown on the demo page).
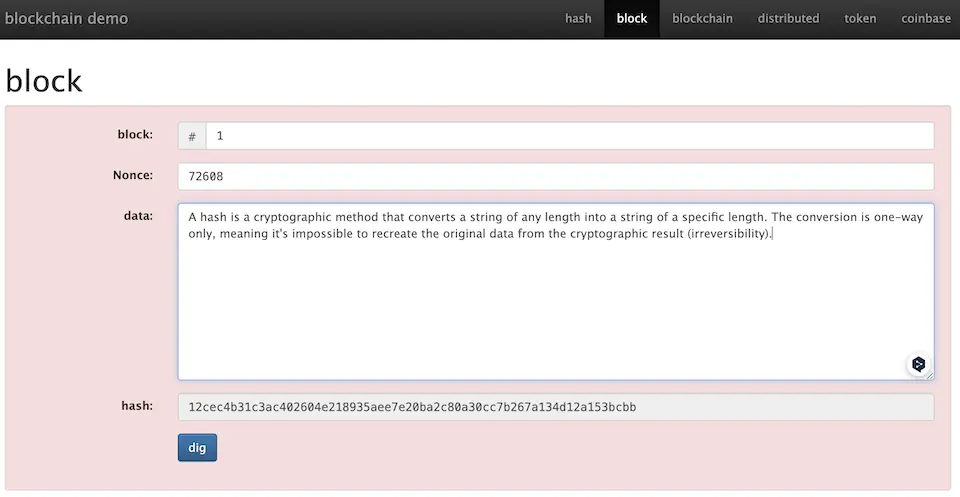
What Does Each Field in a Block Represent?
Block: # … Each block has its own number. Nonce … The nonce is a piece of data used to verify the correctness of the block’s data. Data … This is where the actual data goes. Hash … This is the value obtained by converting the above values using a hash cryptography method.
For this data to be written into the blockchain, it must meet certain conditions. The condition is that the nonce value produces a hash that starts with “0000”. In the case of 72608, the hash value is 12cec…, which does not meet the condition (hence it is highlighted with a red background for clarity).
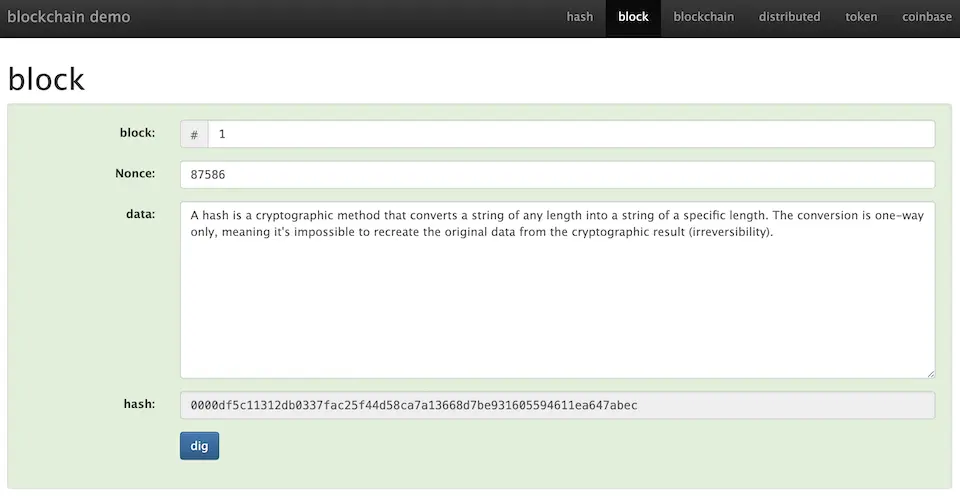
When you press the ‘Dig’ (mining) button, it attempts to find a nonce value that matches the criteria. The result is 87506, and in this case, the hash value starts with 0000, thus meeting the criteria.
Blockchain
A blockchain consists of numerous blocks with a data structure like the one described above, connected together. So, how is this connection represented? (As shown on the demo page) In the next image, there is a field labeled ‘Prev,’ which represents the hash value of the previous block.
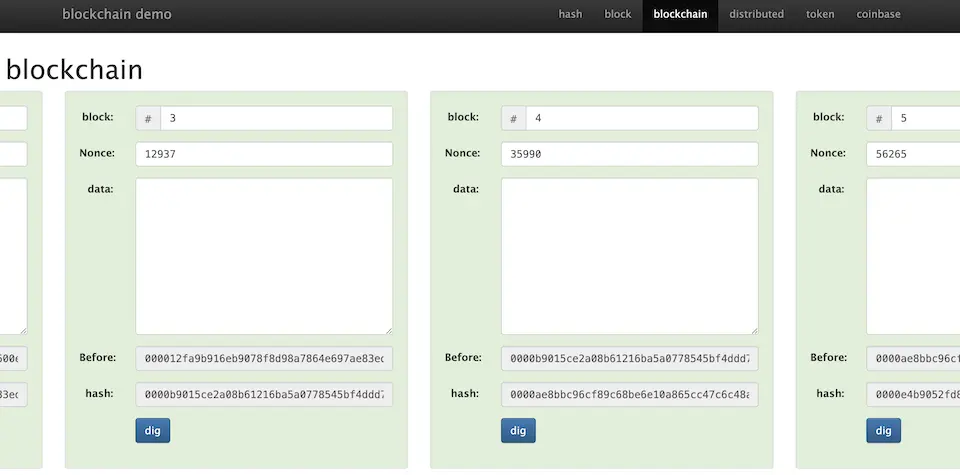
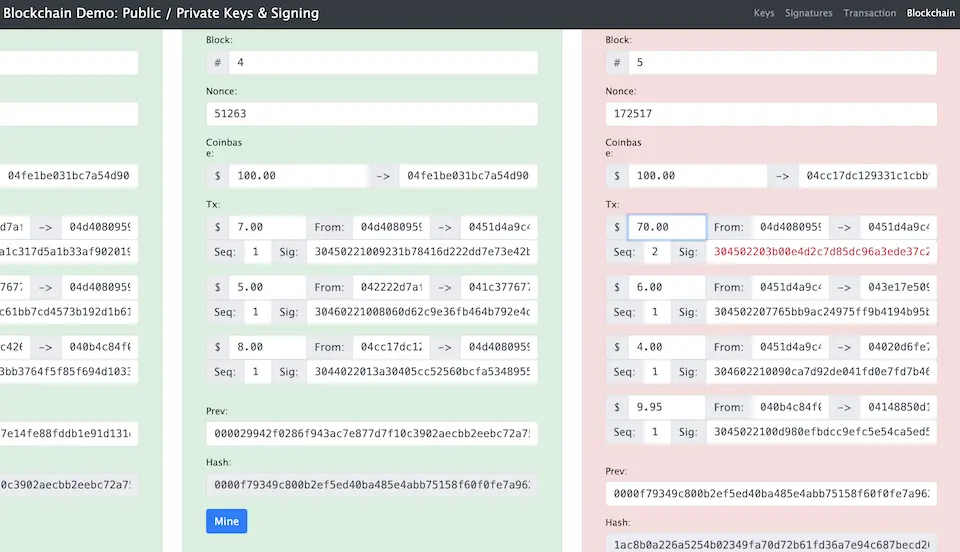
If we try changing the data of the fourth block, as shown in the next image, its hash value changes. Moreover, the change in the hash value of the fourth block also alters the hash value of the fifth block. Consequently, the hash values of both the fourth and fifth blocks no longer start with 0000, failing to meet the condition.
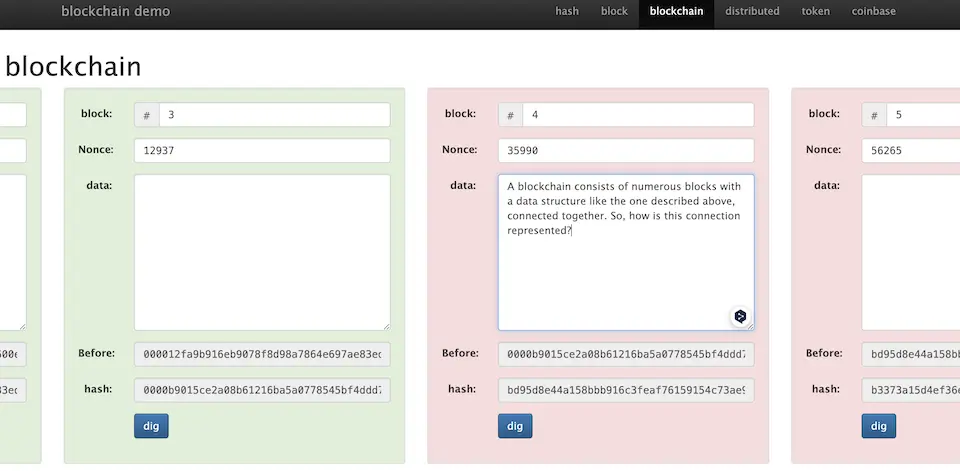
- If the data of a previous block is altered, its hash value also changes. As a result, the hash value of the current block changes too.
- When data in a middle block is changed, it necessitates recalculating the data for all subsequent blocks.
The ‘immutability’ of the blockchain, which I explained earlier, is due to this characteristic. In other words, if you attempt to modify the data at a certain point, it becomes necessary to change all subsequent data.
Decentralization
So far, we have looked at the data structure of the blockchain. These data are distributed and maintained by numerous computers (each node holds identical data). (As shown on the demo page)
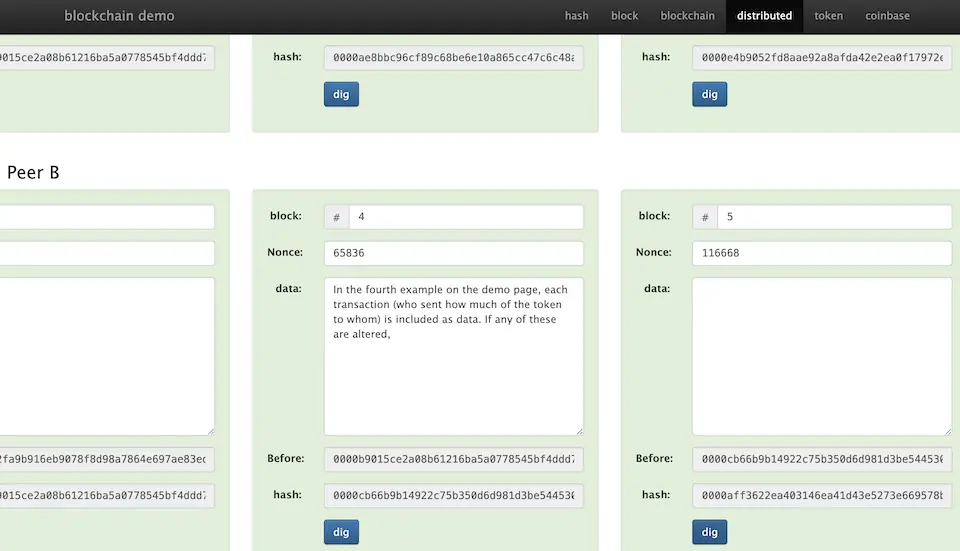
In the above image, let’s assume that the data of Peer B has been tampered with. If we compare the hash values of the fifth block of both Peer A and Peer B, it seems they are different. This means that only the value of Peer B is different, indicating that malicious activity has taken place. In such cases, Peer B would be excluded from the network.
Reference) In the fourth example on the demo page, each transaction (who sent how much of the token to whom) is included as data. If any of these are altered, the same incorrect values or need for recalculation will be detected as in the previous examples.
Public Key Cryptography
Public Key Cryptography
Public Key Cryptography The public key cryptography system enhances the security of data transmission by using two types of keys: a public key and a private key. For example, if person A wants to send a message to person B:
- B creates a private key and a public key.
- A obtains B’s public key and encrypts the message with it.
- A sends the ciphertext.
- B decrypts the ciphertext with their private key.
The public key is generated from the private key (as shown on the demo page).
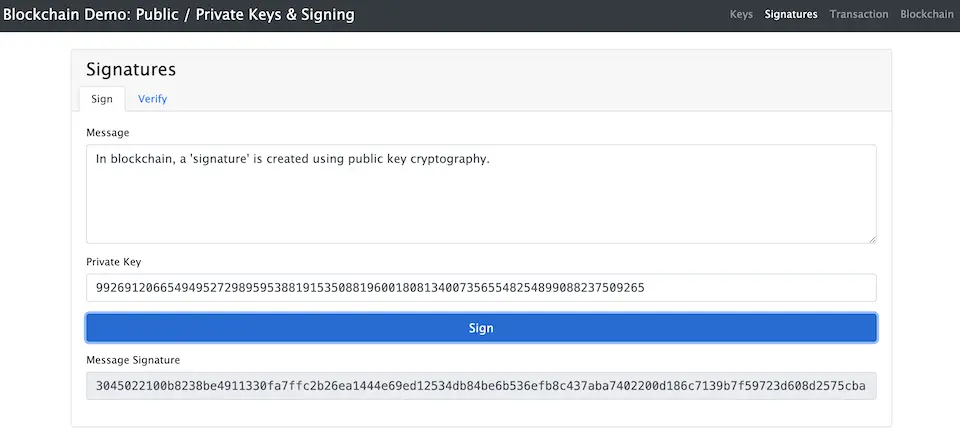
Signature Using Public Key Cryptography
In blockchain, a ‘signature’ is created using public key cryptography. When sending transaction data, the sender encrypts the message with their private key to create a signature (as shown on the demo page).
The recipient of the data receives the message, the public key, and the signature, and verifies whether the received message has been tampered with. In the example shown in the next image, the message received is different from the one signed, and as a result, the verification fails (indicated by a red background). The public key used in this instance is the one that pairs with the private key used for the signature.
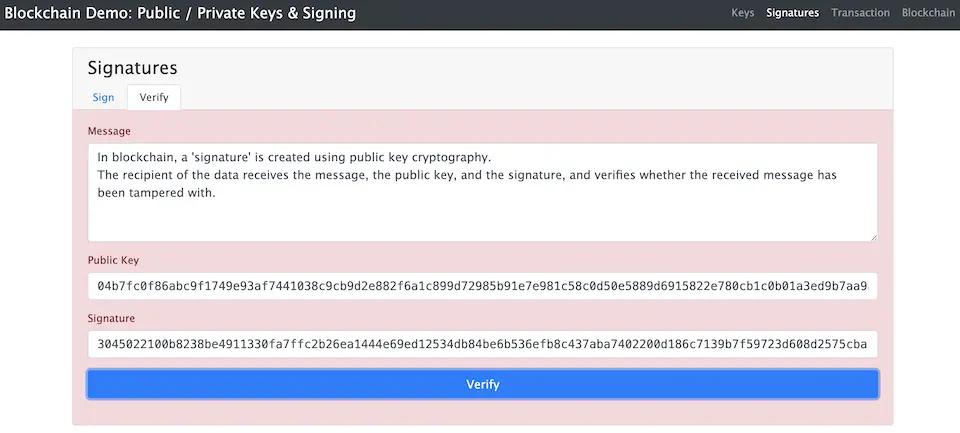
The same mechanism applies even when the above message is transaction data. However, in this case, the entity listed in ‘From’ would be the same as the public key.
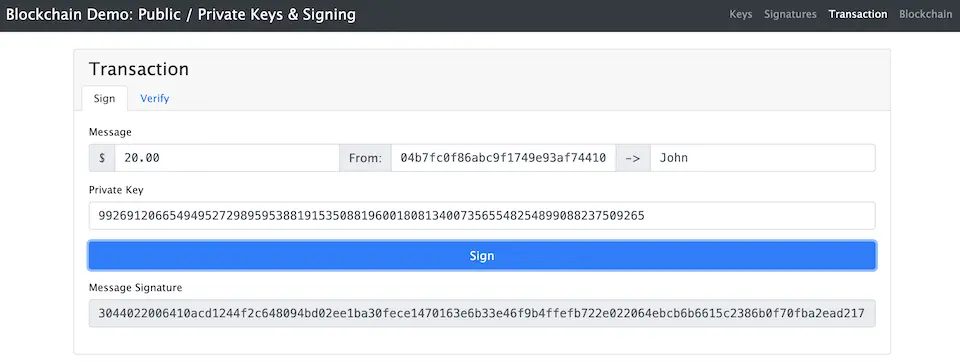
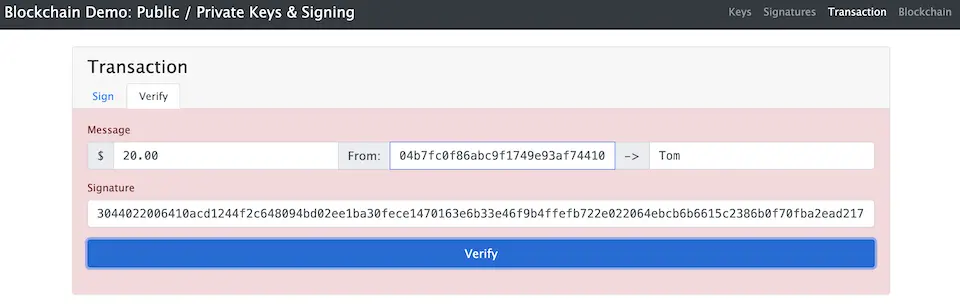
If the verification result is problem-free, the corresponding transaction data is propagated throughout the network and eventually spreads across the entire network.
The content discussed so far is applied in the example on the last demo page. Suppose the total amount of the first transaction in the very last block is changed from 7 dollars; the entire block will be marked as invalid (NG), and the signature of the relevant transaction will also be displayed in red. This indicates an error because the transaction data and the signature value do not match.








Comments